-
Tech Hub StageThe importance of commercialisation in driving innovation in the cyber ecosystemSpeakers
-
Tech Hub Stage
-
Tech Hub StageAI is slipping into your org under the radar, identity attacks are getting smarter, and compliance? It’s a moving target. 2025 isn’t playing nice - and neither should you. Hear directly from Microsoft's security expert (yes, live and in person), alongside Infinity Group and CloudGuard AI, as they unpack the biggest threats and tell you exactly what to focus on (and what to ignore)
-
Tech Hub Stage
Howard will talk about the latest updates in the regulatory landscape and how new legislation is shaping our future. He will talk about how to find easy routes to compliance to help you win more business using regulation and certification as a business enabler. He will also remind you about your responsibilities under the GDPR and why Cyber Essentials is a very powerful business enabler.
Speakers -
Diversity and Skills
Here’s the hard truth: doing great work is no longer enough.
If people don’t see your impact, they can’t benefit from it.
Yet most professionals still shy away from personal branding , thinking it’s about bragging, self-promotion, or being “louder” than everyone else.
That misconception doesn’t just stall careers, it silences leaders and it robs workplaces of the authentic role models they need.
In this talk, I’ll show you why personal branding is the skill every professional needs, whether you’re just starting out or already leading at the top. You’ll discover:
- Why visibility is now as important as performance
- The mindset shift that makes branding authentic, not cringey
- Practical tools to uncover your unique value and communicate it with confidence
- How investing in your brand translates directly into promotions, pay rises, and accelerated career growth
This isn’t about turning yourself into something you’re not. It’s about making sure others see the full value of what you already bring — and amplifying your ability to lead, influence, and open doors for yourself and others.
If you want to future-proof your career and your leadership impact, this is a session you won’t want to miss.
-
Tech Hub StageYou've drafted a policy. It looks nice. It reads well. It aligns with how the team works and is compliant to the standard. But did you forget your dealing with people and not just systems?
A short talk about some investigations as to why policy can fail, and why human nature doesn’t always go along with the plan -
The Gendered Cost of Going Back: The Impact of Return to Office on Women and Carers in CybersecurityDiversity and Skills
-
Tech Hub StageQuantum computing poses an imminent risk to today’s digital infrastructure, with strategies like “harvest now, decrypt later” threatening finance, telecom and defence long before practical quantum computers exist. Meeting this challenge requires quantum-secure communication that is not only technically robust but also commercially scalable.
Photarix is pioneering a breakthrough with compact, room-temperature single-photon sources designed for mass manufacturability and seamless integration with fibre-optic networks. Unlike bulky laser systems or cryogenic quantum-dot devices, Photarix delivers reliable, secure and cost-effective single-photon generation, removing key barriers to large-scale deployment of quantum key distribution (QKD).
-
Tech Hub StageTurn threat intelligence from endless noise into decisive, business-ready action — join this 15-minute talk to learn how to cut through the clutter, focus on what truly matters, and strengthen your defenses where it counts. Discover how to unlock the real-time value of leading cybersecurity solutions — without the heavy price tag — and seamlessly measure and protect your infrastructure across on-prem, cloud, or hybrid environments.
-
Tech Hub StageThe explosive growth of decentralised finance (DeFi) and the Metaverse has opened new opportunities—alongside unprecedented risks. In 2023, over $1.7 billion was stolen from crypto users globally due to fraud, phishing, and smart contract vulnerabilities. Traditional security measures are no longer sufficient to protect users in fast-evolving decentralised ecosystems.
-
Tech Hub StageRoot accounts, master keys, recovery codes.. Where should you store them? How should you keep them safe? How can you ensure access to them when you need them the most? This session explores all the gotchas of this tricky subject.
-
Tech Hub Stage
Traditional pentesting stares into the abyss - snapshots, static reports, false certainty. Blind spots multiply while attackers move faster in the light of the present. This talk breaks the comfort of false confidence and demonstrates how AI-driven continuous pentesting drags security out of the dark, exposing risks as they emerge and arming defenders to move faster, sharper, and earlier than their adversaries.
-
Diversity and Skills
Whilst low-hanging terms like “master/slave” and “black/whitelist” are no longer as embedded in system architecture and team vocabulary, Franky Biles explores how your organisation can go further. By overturning legacy terminology, coding conventions, and everyday expressions in tech and cyber that perpetuate exclusion and bias in security design and recruitment, you'll leave with actionable insights to help build a more inclusive digital future.
Have you ever giggled at ‘Penetration Testing’? Got a graphic sense of ‘male to female’ ports? How might you rephrase ‘Terminated User’ or ‘Repeat Offender’ so your colleagues become a stronger line of defence? And just how would you ‘kill two birds with one stone’?
-
Diversity and SkillsJoin Pentest People and Bulletproof for a panel session to discover how to launch your career in penetration testing. Cyber experts reveal the skills you need, the mindset that gets you noticed, and the opportunities waiting in this fast-growing field. Learn how diverse experiences fuel innovation and why the next generation holds the key to cybersecurity’s future.
-
Diversity and SkillsThe global shortage of cybersecurity professionals is one of the most pressing risks facing organisations today. While the threat landscape grows ever more complex, many businesses struggle to recruit and retain the skilled talent needed to protect their systems and data.
This talk will explore how UK businesses can turn the challenge into an opportunity by leveraging the Government Apprenticeship Levy to fund the training and development of the next generation of cybersecurity experts.
-
Tech Hub Stage"Trust but verify" is no longer just a regulatory mantra, it’s fast becoming a baseline expectation. Compliance frameworks like ISO 27001 and NIST CSF offer structure, but only threat-led testing reveals real vulnerabilities. In a world where breaches move at machine speed and AI is weaponised, TLPT is not a luxury; it’s the proving ground for survival
-
Tech Hub StageSupply chain risk management involves complex business relationships and vast data volumes, yet many organisations still rely on static spreadsheets in shared drives. We examine why Third-Party Risk Management (TPRM) often fails and how strategic collaboration can improve security across your entire supply chain.
-
Tech Hub StageAre you post-quantum ready? Join FullProxy’s cyber specialists as they unpack the NCSC’s roadmap for post-quantum cryptography (PQC). Discover the practical actions you need to take today to ensure you're ready for the quantum leap.
-
Tech Hub StageAs more sectors are drawn into the regulatory net, are new rules enabling or stifling cyber resilience? This session explores how organisations can respond to emerging threats, not just by meeting regulatory baselines but by building true operational resilience. Drawing on recent events, we’ll ask: who didn’t get hit - and why?
-
Diversity and Skills
At today’s crawl, cyber won’t hit parity until 2075, while we face a 4.8 M‑person talent gap and teams with 30 % women see 40 % fewer breaches. Yet just 17 % of CISOs are female.
Ukraine’s Fast‑Track Proof: War drafted the men; thousands of women pivoted into cyber and tech roles in months, showing parity can happen at warp speed when survival demands it.
Session Promise: In 30 minutes, we’ll torch the “slow progress” myth, steal Ukraine’s playbook, and slash 50 years to five.
Key Takeaways
Data > Diversity Talk: Use stats to win board buy‑in.
Mid‑Career Hinge: Sponsor & retain women where the pipeline leaks worst.
Live‑Fire Training Hack: Practical, real-world education (Ukraine‑style) to upskill twice as fast.
-
Tech Hub Stage
Discover how to apply behavioural models such as MINDSPACE and proactive nudges to drive lasting security behaviour change. Learn how to keep security front of mind across your organisation—and how to measure and report its impact effectively to leadership, proving the value of your awareness efforts.
Speakers -
Diversity and SkillsCybersecurity is one of the fastest-growing sectors in the UK, yet women remain significantly underrepresented across all levels. This panel explores the ongoing challenges that deter women and young girls from pursuing careers in cyber, as well as gaining insights from our speakers who have progressed within the cybersecurity industry and how they entered the industry. We'll highlight practical initiatives, partnerships, and outreach programmes that are inspiring the next generation of female cyber professionals, and discuss what more industry, educators, and government can do to build a more inclusive cyber workforce
-
Diversity and Skills
As cyber threats grow in scale and sophistication—driven by automation, geopolitical tensions, and evolving attacker tradecraft—resilience strategies must keep pace. This panel brings together leaders in national infrastructure, cyber defence, and policy to explore how organizations are adapting to a threat landscape where disruption, not just data theft, is the goal.
The discussion will move beyond AI hype to focus on practical resilience measures, including dynamic risk response, Zero Trust integration, and intelligence-led defence. Drawing on current and emerging frameworks and regulations like NIST CSF The Cyber Resilience Act, panellists will share real-world insights into defending critical systems under sustained and advanced attack conditions. -
Diversity and Skills
- Overview – Evolving Threat Landscape
- Why Ai skills matter
- Where will Ai in cybersecurity take us in the next 10 years
- why Ethical Hacking and pen testing need Ai skills today
- how EC-Council helps to enhance Ai skills,
- Why continuous learning in Cybersecurity and Ai is important.
-
Diversity is a driver of innovation and resilience. This session delves into intersectionality and its impact on career progression, team dynamics, and leadership in cybersecurity. Attendees will leave with actionable steps to embed diversity into organisational culture.
Key Takeaways:
Understand intersectionality in the workplace
Learn how diversity influences innovation
Take away policies that promote lasting inclusion -
Diversity and Skills
One of the world leading researchers on anonymisation (and related topics of Statistical Disclosure Control and data synthesis) discusses whether the concept and methods of anonymisation still have a role to play in the world including AI. He discusses his 2014 prediction that Anonymisation would cease to be useful within 15 years whether this looks likely to be true and if so, what do we need to do instead?
Key Takeaways:
- What is anonymisation?
- Is it dead or about to die?
- What do we need to do instead?
-
Diversity and Skills
Most professionals are underpaid, overperforming, and quietly hoping someone will notice. According to Yota Trom, that’s not a strategy—it’s a trap.
In this fireside chat, Yota shares the exact system she’s used to help over 500 professionals—from individual contributors to senior executives—get promoted, negotiate 6- and 7-figure salary increases, and finally speak about their value with confidence.
Listeners will discover:
- How to uncover their true market value (and back it up with data)
- A step-by-step approach to asking for a raise or promotion—without the cringe
- How to build visibility with personal branding that feels authentic, not salesy
Packed with real stories, scripts, and mindset shifts, this conversation goes far beyond typical career advice. Whether you’re early in your career or already leading teams, Yota’s insights are a wake-up call, a confidence boost, and a practical guide to owning your ambition and asking for what you deserve.
Get ready to stop waiting for recognition—and start getting it.
-
Diversity and SkillsIn high-stakes security environments, cybersecurity teams require inclusive leadership for effective decision-making and team resilience. This session explores how inclusive leaders navigate the personnel challenges in the cyber landscape: building trust during security incidents, exploring diverse perspectives for stronger threat detection, and creating teams where everyone can contribute their best work when it matters most. Learn why inclusive leadership strategies strengthen both your security posture and your people.
-
Diversity and SkillsThis session looks ahead to the future of cyber talent. What are the next challenges—and opportunities—for making cybersecurity a truly inclusive and skilled profession? Industry leaders weigh in on the road ahead.
Key Takeaways:
Anticipate future talent needs in cyber
Learn how to scale inclusive practices
Explore collaborative solutions for long-term diversity -
Tech Hub StageDiscover how Secure Access Service Edge (SASE) can transform your security architecture by unifying network and security services into a cloud-native platform. Learn how SASE enhances web security, streamlines remote user access, and supports a modern, scalable, and secure digital workplace
-
Diversity and Skills
Building inclusive pathways into cyber requires intentional design — from outreach to executive development. This session explores how to attract and grow diverse talent without relying on outdated models.
Key Takeaways:
Create frictionless entry for untapped talent
Promote equity in career progression
Align hiring with long-term capability
Enhace your USPsSpeakers -
Diversity and SkillsMental health is a critical part of cyber resilience. This session explores how stress, burnout, and isolation affect cybersecurity professionals—and what employers can do to build psychologically safe, supportive work environments.
Key Takeaways:
Recognise wellbeing risks in high-pressure cyber roles
Learn strategies to support mental health in the workplace
Understand the ROI of wellbeing on performanceSpeakers -
Diversity and SkillsWhat does it take to build truly inclusive leadership in cybersecurity? This session brings together senior leaders to share success stories, breakthrough moments, and the systemic changes that are transforming our industry. Discover how effective allyship, sponsorship, and inclusive leadership practices are not just retaining diverse talent - they're driving better security outcomes. Through personal journeys and practical strategies, learn how to create breakthrough moments for others and build stronger, more effective cybersecurity programs.
Key Takeaways
Explore proven strategies for breaking through barriers and creating breakthrough moments in cybersecurity leadership
Learn actionable allyship and sponsorship techniques that drive career advancement and team performance
Understand how inclusive leadership visibility transforms team dynamics and delivers measurable security outcomes
Gain practical tools you can implement immediately to champion inclusive leadership in your organization -
Diversity and SkillsCybersecurity starts with the basics. This session explores how community-driven education and foundational training help underrepresented groups gain access to the cyber industry, empowering future professionals while improving overall cyber resilience.
Key Takeaways:
Understand the importance of foundational cyber education
Learn how to engage underserved communities
Explore grassroots training and mentorship initiativesSpeakers -
Diversity and Skills
Cybersecurity careers are as diverse as the threats we face. This panel brings together hiring managers, educators, and security leaders to explore what employers are really looking for today—from technical skills to adaptability and AI literacy. Learn how certifications, hands-on experience, and non-traditional pathways are shaping the modern cyber workforce—and how to position yourself in a skills-first market. The session will include extended audience Q&A, offering a chance to gain personalised advice, guidance, and insight directly from seasoned professionals.
-
Tech Hub StageThis session explores strategies to strengthen cyber resilience by addressing the full threat spectrum—from human error to ransomware. It highlights the importance of security awareness, proactive defenses, and incident response planning, empowering organizations to mitigate risks, safeguard data, and maintain business continuity in an increasingly hostile landscape.
-
Tech Hub StageThis session explores how generative AI tools like Claude 4 revolutionise vulnerability assessment. Discover how cutting-edge AI streamlines threat detection, prioritises risks, and enhances attack surface protection—empowering security teams to work faster, smarter, and more effectively in today’s evolving cyber threat landscape.
-
Tech Hub StageIn an era of escalating threats, just as military forces rigorously train to ensure readiness and integration, the private sector must embrace the same ethos of continuous, tested development. This talk explores why exercises, ranging from tabletop scenarios to advanced cyber range simulations, are essential for assessing and strengthening cyber resilience across people, processes, and technology. It highlights how these exercises foster collaboration, sharpen incident response, and bolster supply chain resilience, while also demonstrating the necessary operational readiness needed to meet the stringent compliance requirements of the Cyber Resilience Act, NIS2, DORA and similar legislation.
-
Tech Hub StageJake will delve into the darker, more controversial aspects of facial recognition technology, exposing its unsettling potential. He'll unveil cutting-edge glasses capable of real-time identification, allowing you to discover someone's identity with nothing more than a glance. But it doesn't stop there — Jake will also demonstrate how AI can be used to outsmart these systems, revealing how he successfully bypassed a bank’s supposedly secure facial recognition system using nothing but freely available software. For the grand finale, Jake will push the boundaries even further. He’ll add himself to a high-security watchlist of known suspects - only to walk straight past the system undetected with the use of AI, proving just how vulnerable and exploitable this technology truly is.
-
Tech Hub Stage• Trends and Emerging Cybersecurity Risks – An overview of the latest threats and vulnerabilities in cybersecurity, from advanced attack methods to evolving tactics used by threat actors.
• The Evolution of Cybersecurity: Are We Doing Something Wrong? – A critical look at today’s security strategies, identifying key gaps and exploring innovative ways to stay ahead.
• AI in Cybersecurity: Risks and Opportunities – Exploring how AI is reshaping both cyber threats and defense, and what steps organizations must take to use it effectively while reducing risks -
Tech Hub StageAn overview of Datambit’s Deepfake Detection Solutions for Audio and Video deepfakes will be presented, as well as the use cases Datambit is targeting. An overview of the ease of use and deployment of the solution will be discussed. The tenants of performance and trust that the Company is built upon will be explained
-
Tech Hub StageThe human factor remains cybersecurity's most critical, yet often overlooked, element. This keynote dives into the fascinating psychology of trust – how we build it, how it's exploited, and whether we should even try to validate it in a digital world. From a grandmother's Facebook recipe group to a North Korean fake IT worker infiltrating a tech company, this presentation will explore real-world tales of social engineering. It will unpack why human brains are wired to fall for scams, and how AI is blurring the lines of reality, and how we can navigate the modern trust paradox.
-
Tech Hub StageThis presentation addresses the urgent need to future-proof digital security against emerging quantum computing threats, which enable "harvest now, decrypt later" attacks by allowing adversaries to collect encrypted data today for future decryption. Co-Founder and CTO of Senetas, Julian Fay will explain how high speed encryptors provide a robust and high-performance solution, designed to protect data as it travels across various network types. This includes a simplified guide to Post-Quantum Cryptography (PQC), detailing how our encryptors implement NIST quantum-resistant algorithms through hybrid key establishment and inherently quantum-safe Transport Independent Mode, alongside support for Quantum Key Distribution (QKD). Attendees will gain insight into why proactive preparation is critical now to safeguard sensitive information, leveraging our globally certified and future-ready encryption portfolio.
-
Global Cyber SummitGeopolitical turmoil continues to define 2025. In addition to the ongoing war in Ukraine and the tragedy unfolding in Gaza, rising tensions between India and Pakistan, as well as the often-overlooked …Chairperson
-
Global Cyber SummitThis session will address the ongoing skills crisis affecting industries worldwide, with a focus on identifying root causes and understanding its impact on business performance. We will explore effective strategies for bridging the skills gap, including talent development, reskilling, and innovative recruitment approaches. The presentation will also highlight the role of leadership and organisational culture in fostering a skilled, adaptable workforce ready to meet future challenges. Practical insights and case studies will equip participants to navigate and overcome the skills shortage in their own organisations.ChairpersonSpeakers
-
Global Cyber SummitThis session will demystify professional recognition in the cyber security field and explain why it matters for your career development and credibility. We will learn what it takes to submit a success …
-
Global Cyber Summit
As cybercrime becomes more sophisticated and widespread, traditional law enforcement faces new pressures to adapt. This session examines how we are evolving to meet the demands of the digital age, tackling issues like data breaches, online exploitation, and digital evidence collection. Charlie will discuss real-world investigations, challenges in attribution and jurisdiction, and the importance of collaboration with cybersecurity professionals and tech companies. We will gain a deeper understanding of how law enforcement is working to stay ahead of cybercriminals and where the gaps remain.
-
Global Cyber SummitIf the buzzword for 2024 was resilience, 2025's is collaboration. In a world of political turbulence, constant technological innovation and ever more complex threats, sharing data, threat intelligence, experience, knowledge and expertise becomes even more important. Organisations are now interdependent and reliant on capability provided by third parties. Supply chains are critical to an organisation's ability to operate, and attacks are often indiscriminate in what and where they harm. Protecting ourselves is often not enough when our suppliers may well provide the access point through our defences, particularly if they lack the capacity or knowledge to protect themselves. Collaboration is, however, easier said than done. It thrives on trust and strong relationships and requires constant investment in time and effort ' rather like resilience.ChairpersonSpeakers
-
Global Cyber Summit
Are you curious as to how impactful leaders seem to effortlessly control a meeting, a discussion or even a room no matter how technical the subject? What tips and tricks are they using that you could incorporate to ensure that you also lead with impact. Then join this session where Cheryl will discuss some of the techniques that she has used in the very technical world of cyber and how she has coached and mentored individuals and teams to unlock their potential.
-
Global Cyber SummitWe continue to witness a bewildering array of new technologies, each promising significant benefits, but not without risk. Keeping pace with innovation is a challenge for most organisations. Understan …Speakers
-
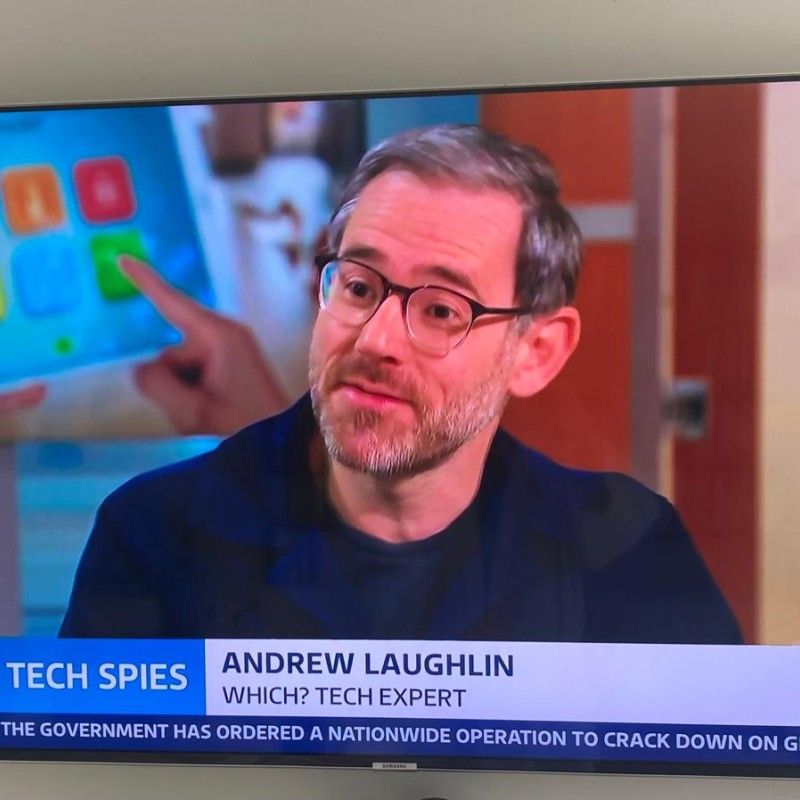
Global Cyber Summit
In this fireside chat, Dr Zimeta, Head of Digital and Data Policy at Which?, and Andy Laughlin, an investigative journalist, will explore the intersection of tech scrutiny and policy advocacy in consumer technology. Andy will share insights from years of investigative work uncovering how smart home devices and apps collect excessive and often unclear data, such as in the viral “Why is my air-fryer spying on me?” exposé. Dr Zimeta will discuss how these revelations shape the policy landscape, from influencing regulators like the ICO to setting future priorities for product security. Together, they will offer a lively and thought-provoking look at how journalism and policy can work hand in hand to protect consumers in an increasingly connected world.
-
Global Cyber Summit
An overview of the Cyber Growth Action Plan, covering how it will strengthen the British cyber ecosystem
-
Global Cyber SummitThis presentation will uncover why burnout is the hidden crisis quietly undermining your team's potential. It will explore how to identify the early signs of burnout before they derail projects and mo …
-
Global Cyber Summit
Cybersecurity is no longer a binary state of “secure or not secure.” An organization’s posture depends on its risk appetite and how it manages third-party dependencies. Traditional vendor risk assessments — from self-assessments and audits to certifications — offer partial insight but often lack transparency and objectivity. In this fireside chat, we’ll explore the challenges of Cyber Rating & Third-Party Risk Management (TPRM), highlight innovative approaches for understanding vendor security posture, and present how transparent, inside-out measurement is already being adopted across the Spanish financial sector and beyond.
-
Global Cyber Summit
In an increasingly interconnected global economy, the resilience and reliability of supply chains have become critical to business success. This presentation examines the vital role of third-party assurance in managing supply chain risk, ensuring compliance, and maintaining stakeholder trust. It explores key frameworks, emerging standards, and real-world case studies that demonstrate how independent verification can uncover vulnerabilities, enhance transparency, and drive continuous improvement. We will gain insights into best practices for evaluating third-party partners, mitigating operational and reputational risks, and fostering a culture of accountability throughout the supply network.
-
Global Cyber SummitAs geopolitical tensions rise and AI adoption accelerates, the nature of cyber threats is becoming increasingly complex and difficult to detect. This presentation explores the emergence of invisible AI-powered risks and their impact on national security, equity, and ethics. Drawing on real-world case studies, it highlights the need to strengthen cyber resilience through AI-driven threat detection, business continuity planning, and global collaboration. It also underscores the importance of a human-centric approach that prioritizes education, awareness, and adaptability to stay ahead of rapidly evolving threats in a connected digital world.Speakers
-
Global Cyber Summit
In this fireside chat, Gordon will discuss his new book, The Spy in the Archives. This session will explore the real-life espionage and historical research that informed the book, revealing how hidden records and overlooked details can reshape our understanding of intelligence, security, and international affairs. With reflections on the craft of research and the enduring relevance of archival material, this session offers a compelling look at the intersections between history, secrecy, and statecraft.
)
)