Fighting Cyber Attackers Earlier to Reduce Risk

We face an exciting evolution in the cybersecurity sector.
Attackers are becoming both more efficient and intelligent at evaluating their targets and successfully carrying out their intended campaigns. Often money is at the forefront of their minds but, as we have seen recently, drivers may also be geo-political or activist views. Whatever their motivations, financial or otherwise, their methods continue to be both immoral and, in most jurisdictions, illegal. Understanding and tackling these threats becomes ever harder for organisations.
.jpg)
Enter reconnaissance. The first stage described in dedicated frameworks such as MITRE ATT&CK or Lockheed Martin Kill Chain is that of reconnaissance. The period when an attacker will be gathering valuable data in order to enable them to understand where they might best focus their activities to create maximum value for their aims. Reconnaissance can take many forms such as searching social media to understand more of the psychology of the situation, the main players, what they like and dislike, their movements and interactions so that a social engineering approach can be created. Understanding what external exposure there might be for computer systems also potentially shows areas of misconfiguration or technical vulnerability that could enable a successful attack. Understanding the latest vulnerabilities across the wider infrastructure such as networked printers, uninterruptible power supplies, VPN servers or back-end business critical application servers can give an attacker a valuable insight into where to devote their time. Searching the dark web for potentially previously exfiltrated lists of users and passwords might be another area of focus for an attacker as they piece together the various sets of data that enable them to form an attack plan.
The availability and evolution of such attacks alongside the ever-increasing speeds of internet connectivity all serve to make understanding the reconnaissance phase even more critical for the defenders. Their aim is to lower their time to detect (TTD) and time to remediate (TTR). We often see data exfiltration prior to the deployment of ransomware along with backups being deleted and data encrypted so identifying these critical metrics should be front and centre of all organisations’ planning and prioritisation.
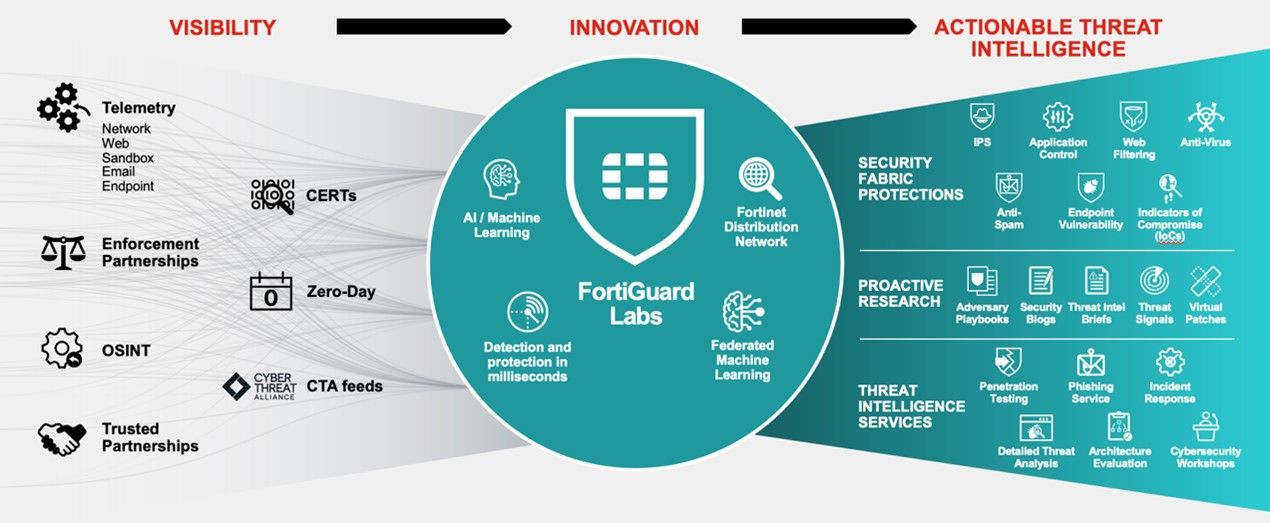
To combat the attacks and ensure attackers are discovered in minutes rather than days or months organisations have a multitude of toolsets and components open to them. A key part of the challenge is picking solutions that enable the teams to understand the risks and reduce aspects such as alert fatigue so that the resulting solutions are more sustainable, auditable and beneficial. Encouraging efficiencies and better collaboration amongst often disparate teams can also be a potential positive side effect of solving these challenges.
Of the variety of toolsets available two aligned to the reconnaissance phase are deception and digital risk protection services. We will delve into these to illustrate the potential benefits organisations could derive from them.
Firstly, deception can add huge value and provide invaluable telemetry. This can enable your organisation to react quickly whilst also learning about the attacker’s tactics, techniques and procedures. This allows teams to gain the knowledge to adjust defences in line with the changing attack vectors in use at that time. Deception can also be used where critical workloads are being moved into the public cloud and project teams want an early warning system in place to account for the potential of misconfiguration of the associated security controls within the cloud provider as is often seen. A multitude of decoys is possible to enable a full spectrum replica to be created. Decoys such as printers, uninterruptible power supplies, ESXi servers network shares and custom decoys are all possible. Deploying fake but highly convincing decoys around the network can enable risk-averse automation (where an attacker is quarantined as soon as they so much as even ping a decoy) through to more risk-accepting ones (where SOC teams can watch what an attacker does in intimate detail for an extended period to understand motivations and behavior). For example, an attacker might put a dropper file into a decoy thinking they can use a zero-day exploit in a critical business system to achieve their objectives. The reality would be that the deception platform would talk to the sandbox to have the zero-day exploit forensically analyzed and immediately the new security intelligence would be distributed around the broader infrastructure to protect the network, users, and data from this new risk.. Deception is now a key shield for organisations seeking to expand their capabilities and defeat their attackers much earlier in the cycle.
Secondly, Digital Risk Protection Services are a way to expand the visibility of organisations beyond their electronic boundaries and get a more global vision of what attackers can see. Being able to understand the external attack surface can help remediate problems before they escalate. Examples include: helping protect brand reputation linked with, for example, typo domain squatting, website copies, rogue app monitoring, dark web information sales and social media posts. Having this level of visibility can replicate the attacker’s viewpoint and enable organisations to close holes, increase the difficulty and lower the risk.
.jpg)
Increased visibility and better intelligence are, of course, less valuable if there is no easy way to distribute that critical knowledge across the overall infrastructure. As Gartner recently stated, a Cybersecurity Mesh Architecture (CSMA) is crucial to enabling organisations to better equip themselves with a sustainable cybersecurity capability. Deception and Digital Risk Protection Services are just two examples of the new technology solutions that Fortinet can provide to customers. The Fortinet Security Fabric is the globally proven platform by which the entire infrastructure, regardless of location, is protected in an instant to dramatically lower risk, increase visibility, improve efficiency and lower alert fatigue across the operational teams.
If you’d like to know more then please drop by at stand G50 at International Cyber Expo and do not miss our Product Innovation session on FortiDeceptor on 27th September at 13:45-14:05.
)
)